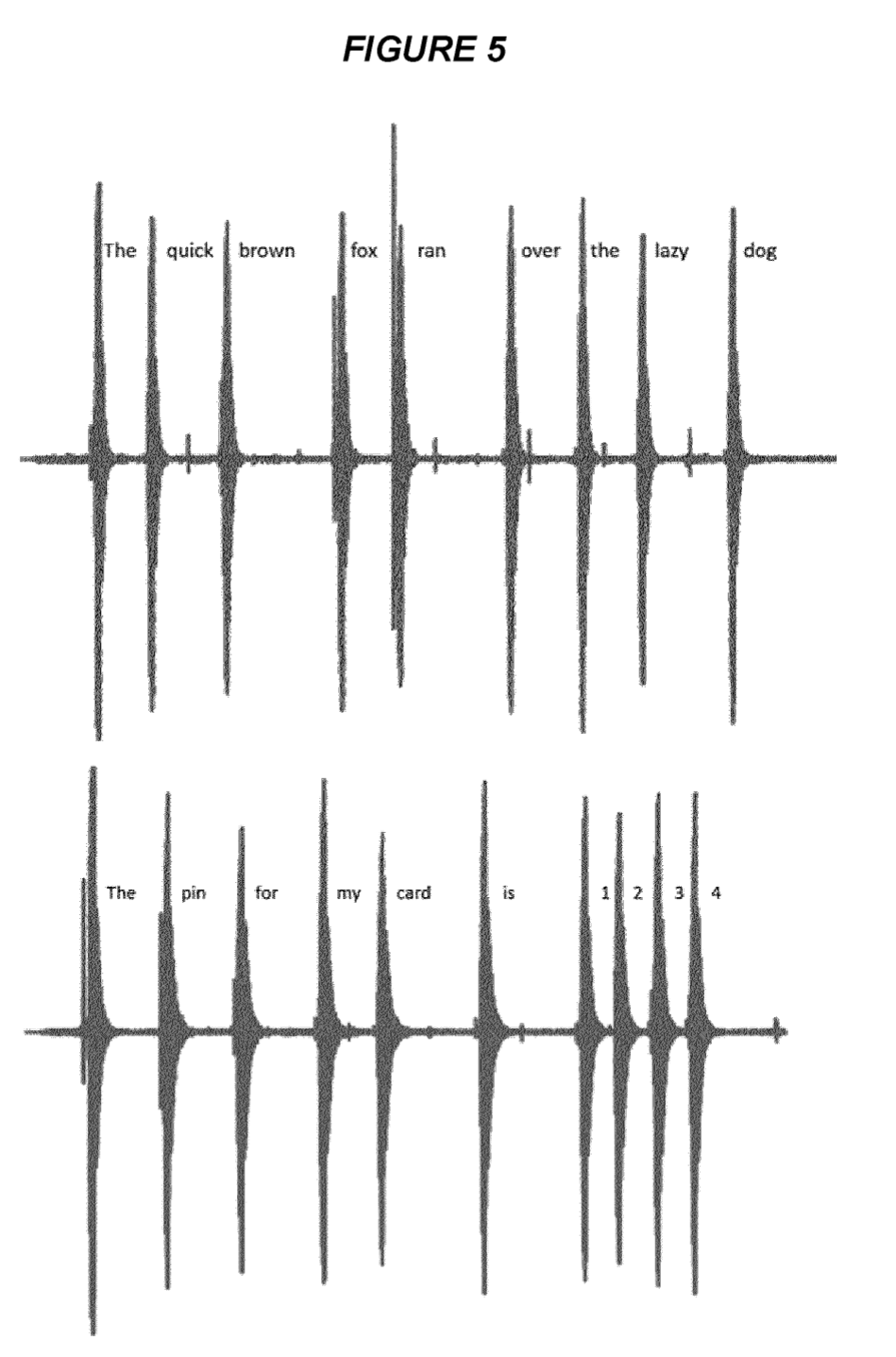
Sensors | Free Full-Text | Behavioral Acoustic Emanations: Attack and Verification of PIN Entry Using Keypress Sounds

Modeling extreme values resulting from compromising electromagnetic emanations generated by an information system - ScienceDirect
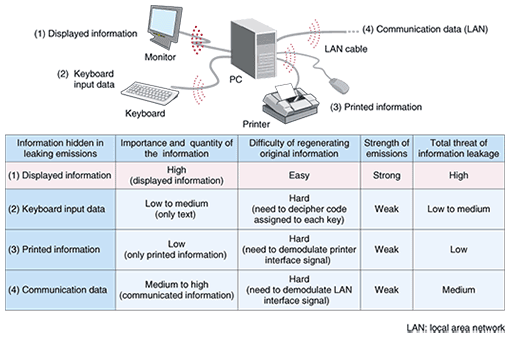
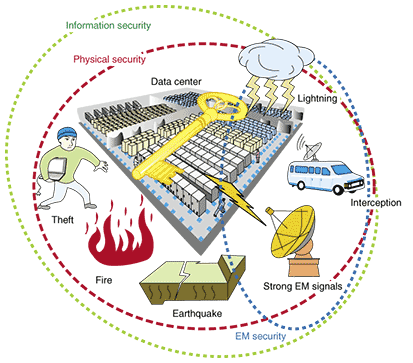
Countermeasures to Prevent Eavesdropping on Unintentional Emanations from Personal Computers | NTT Technical Review

Radon Emanation Measured Data Along a Traverse Crossing Ahwaz Fault... | Download Scientific Diagram

Archive Series - Volume 1 - Emanation | Sam Rivers, Cecil McBee, Norman Connors | NoBusiness Records
Unintentional Compromising Electromagnetic Emanations from IT Equipment: A Concept Map of Domain Knowledge
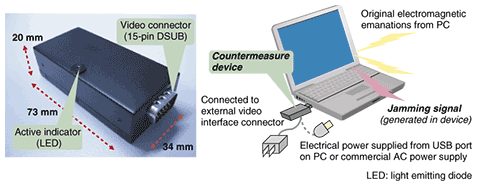
Countermeasures to Prevent Eavesdropping on Unintentional Emanations from Personal Computers | NTT Technical Review