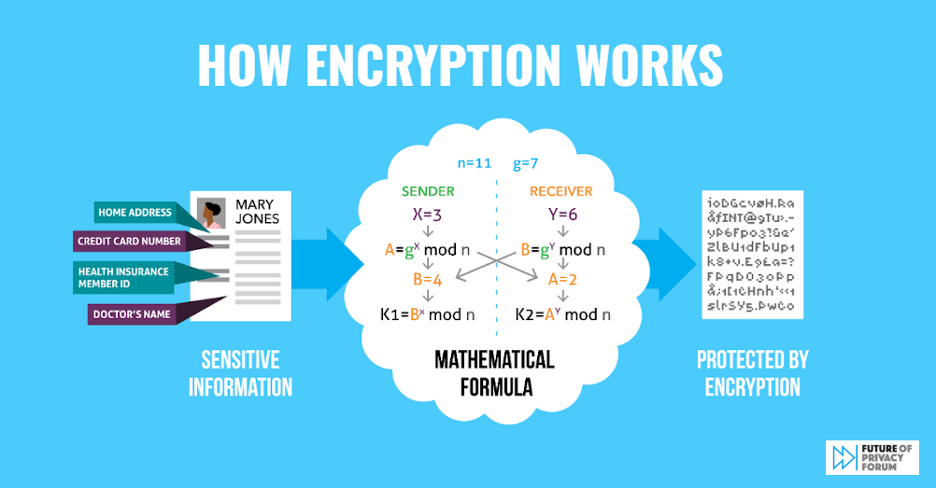
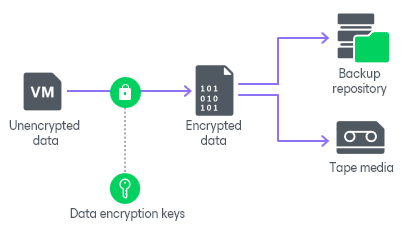
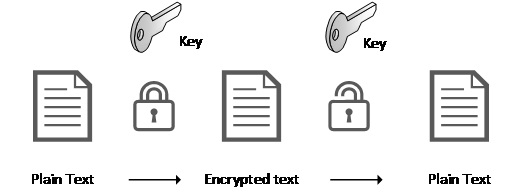
Managing Encryption for Data Centers Is Hard. And It Will Get Harder | Data Center Knowledge | News and analysis for the data center industry
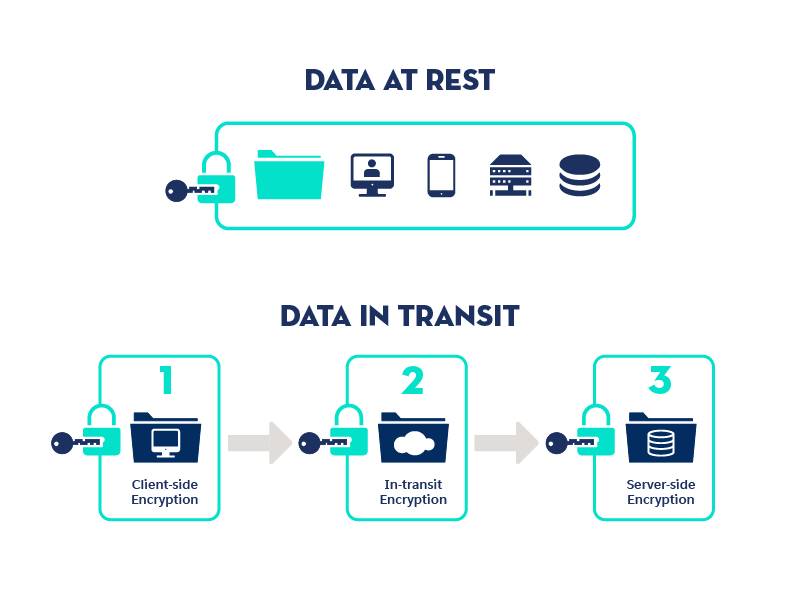
Rethinking data security: 5 ways encryption can help to protect your data - ZNetLive Blog - A Guide to Domains, Web Hosting & Cloud Computing