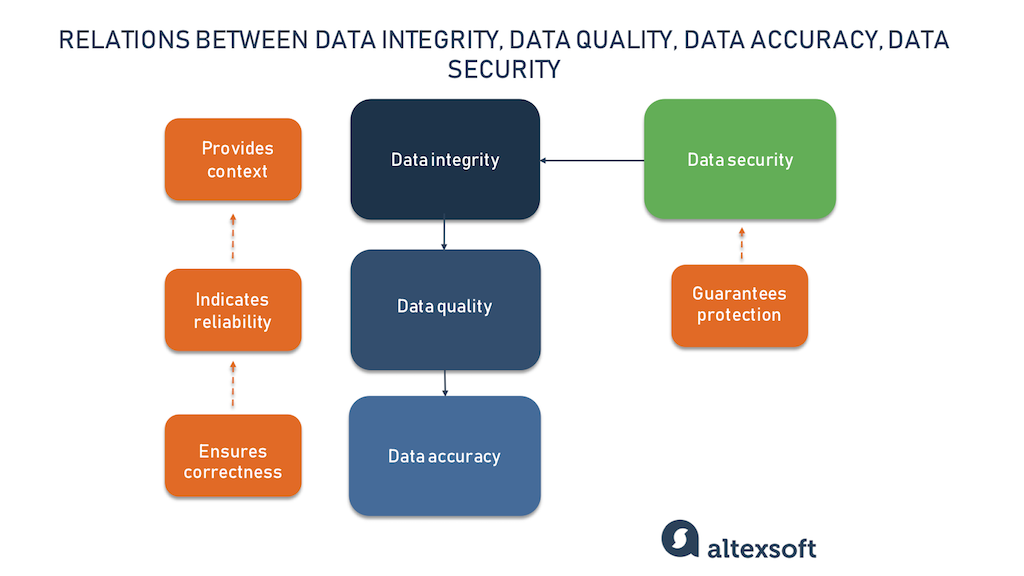
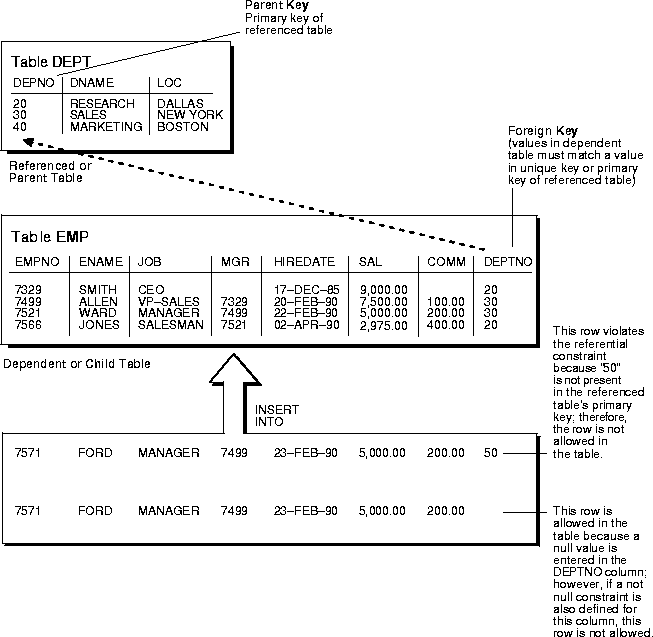
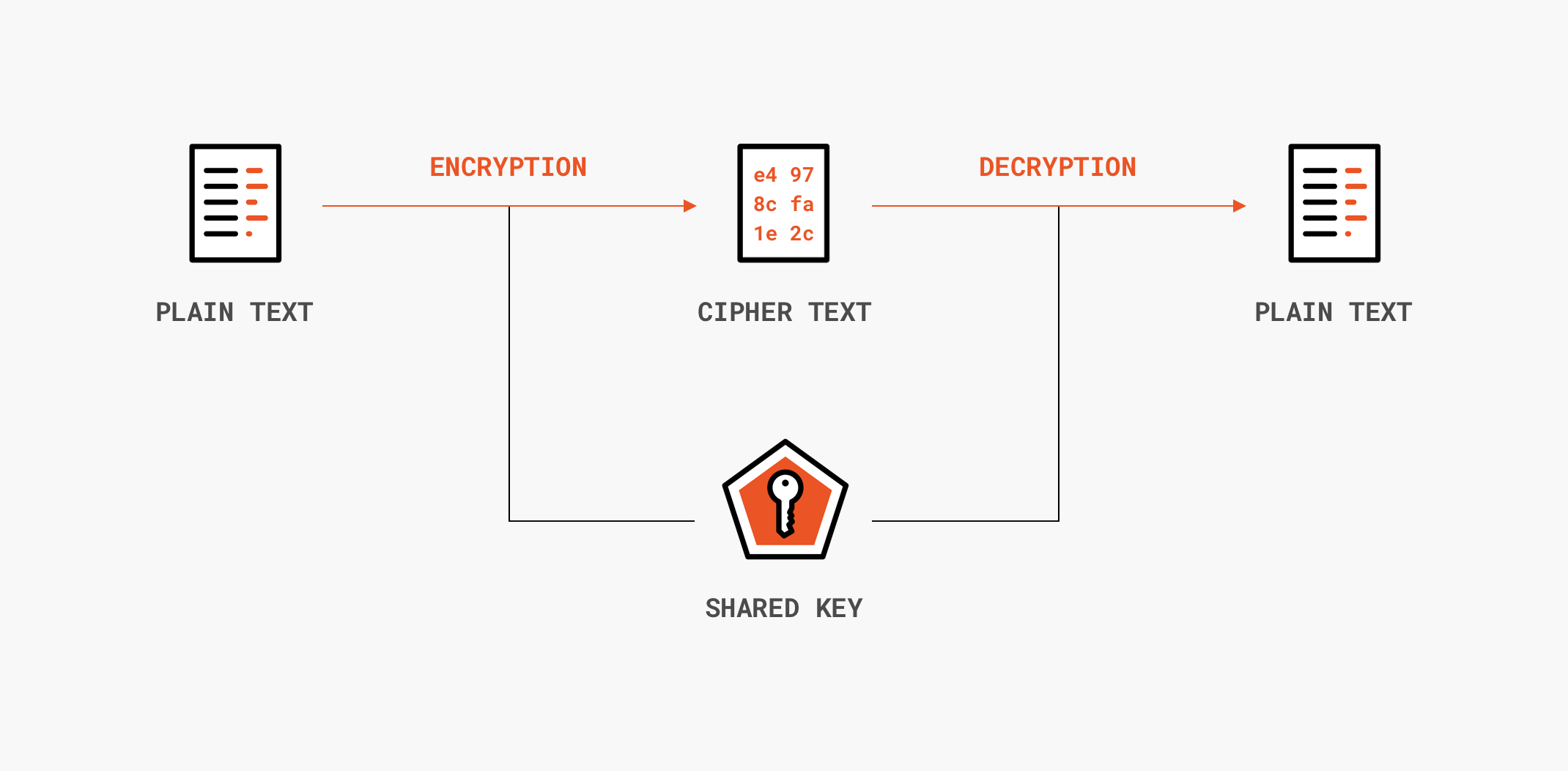
When it Comes to Data Integrity, Can We Just Encrypt the Data? - EngineerZone Spotlight - EZ Blogs - EngineerZone

Asymmetric cryptography - ensuring data integrity, confidentiality and... | Download Scientific Diagram

When it Comes to Data Integrity, Can We Just Encrypt the Data? - EngineerZone Spotlight - EZ Blogs - EngineerZone