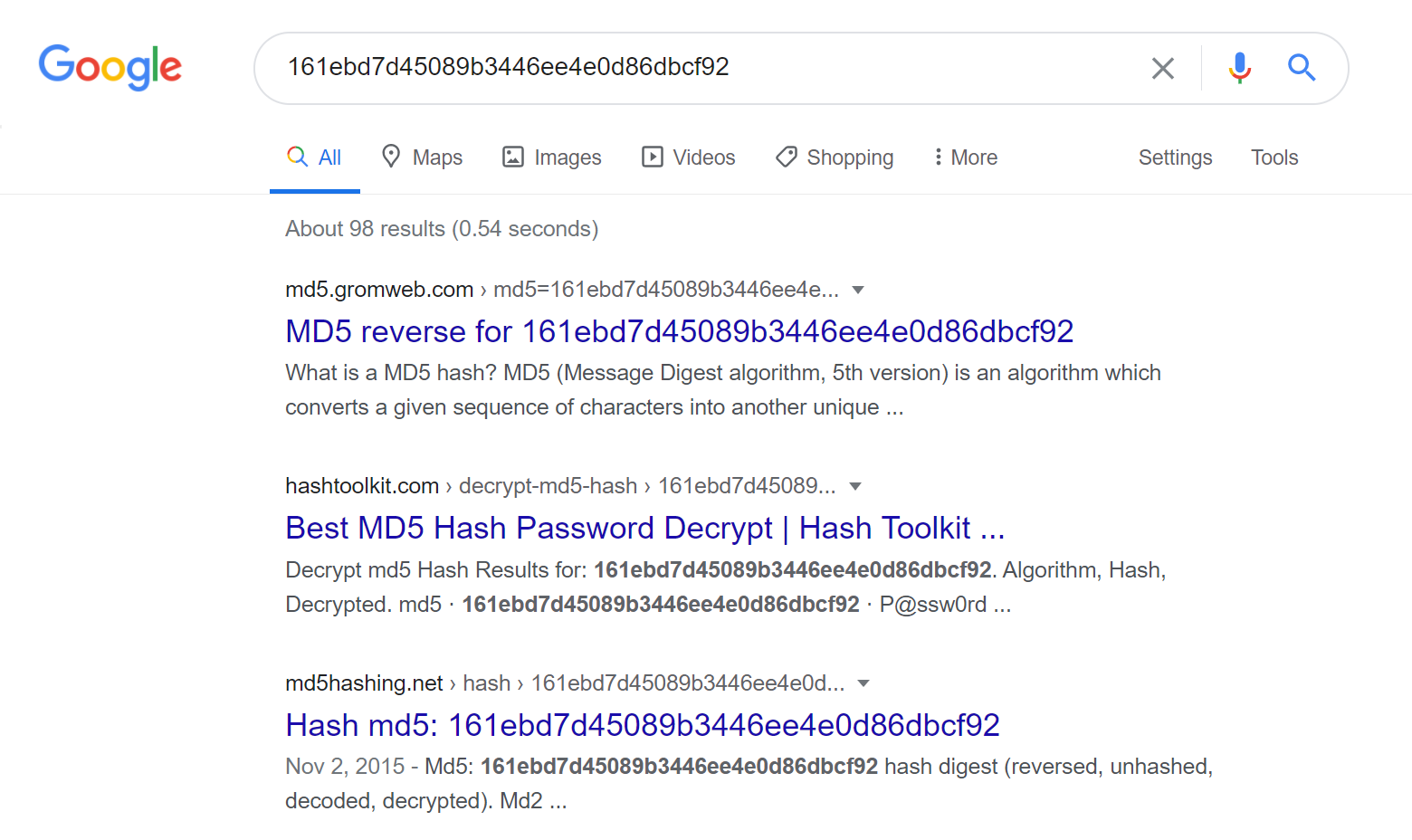
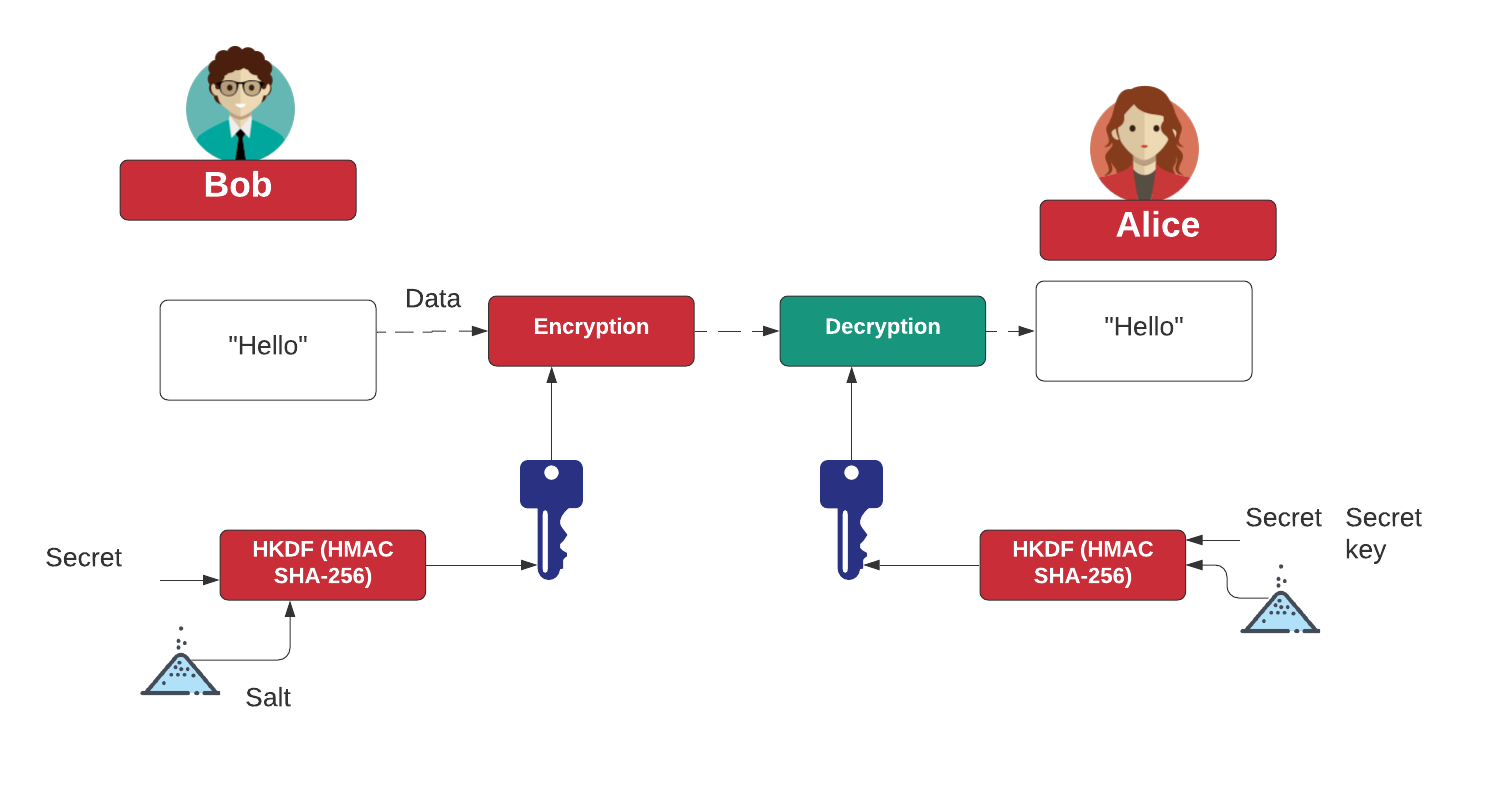
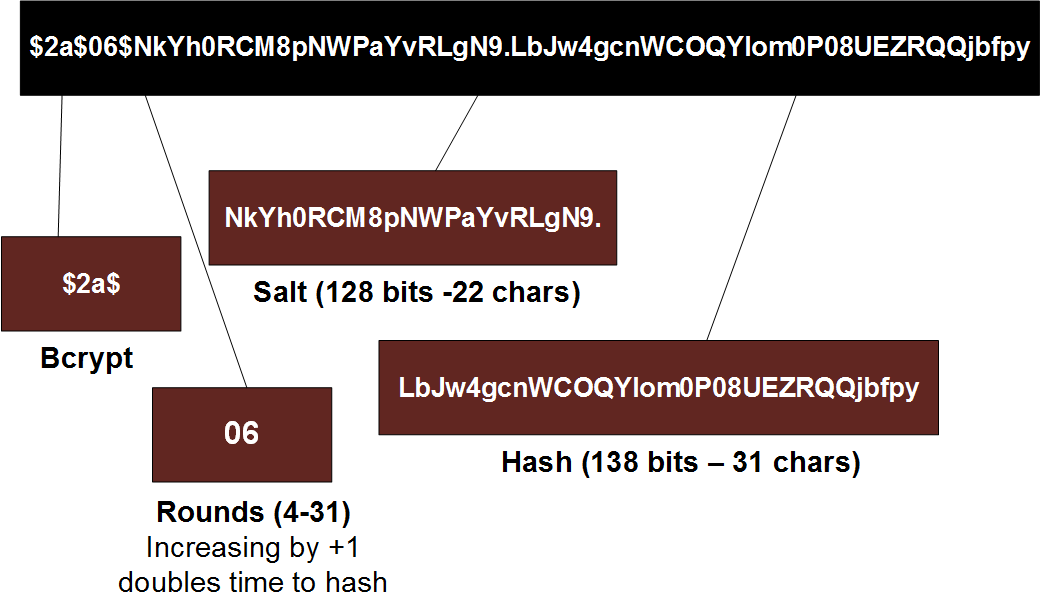
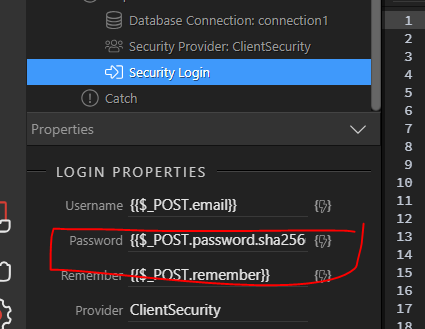
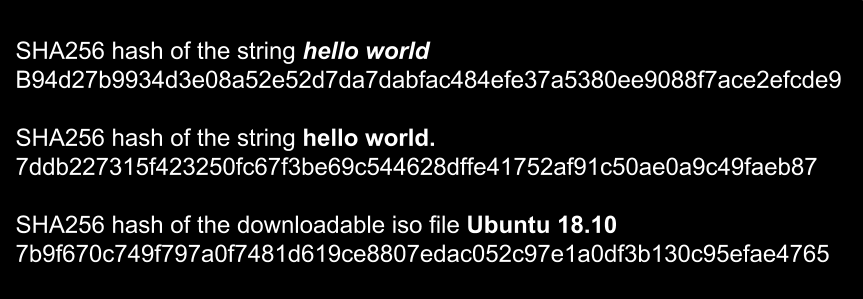
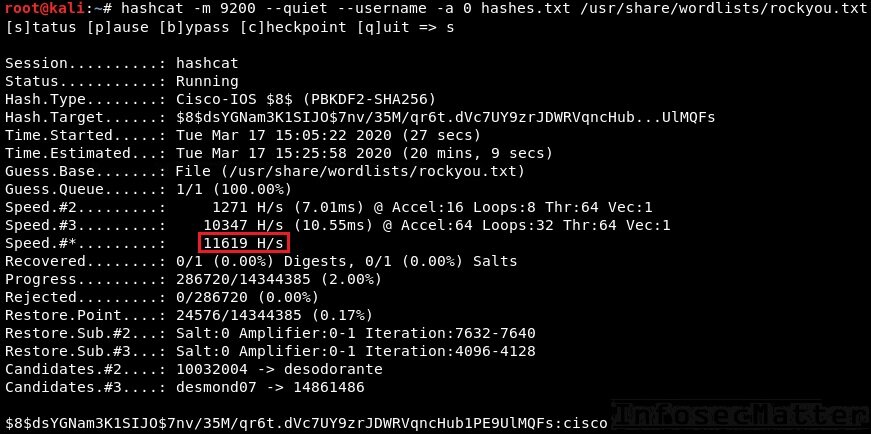
Passwords and hacking: the jargon of hashing, salting and SHA-2 explained | Data and computer security | The Guardian

java - Encryption and Decryption with PBKDF2 and AES256 - practical example needed - how do I get the Derived key - Stack Overflow

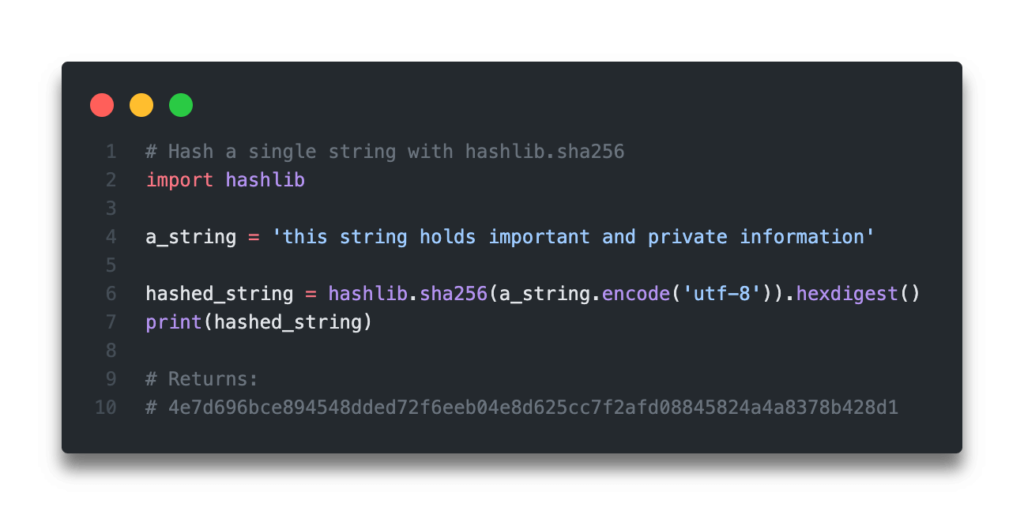
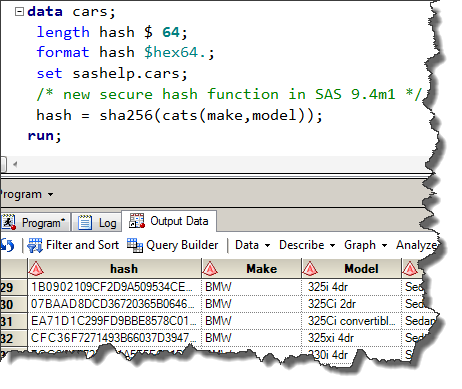
SHA 256: Compute a SHA 256 hash using C# for effective security - .Net Core | MVC | HTML Agility Pack | SQL | Technology Crowds